Introduction
Madigan Solutions' user management tool (UMT) is a tool designed to manage the life-cycling events of identities that fall outside of HR processes and systems, e.g., contractors, suppliers, work experience students, guests, non-human identities, etc.
The platform is provided as a Software-as-a-Service (SaaS) offering so to get started with UMT, you only need an email address and a browser.
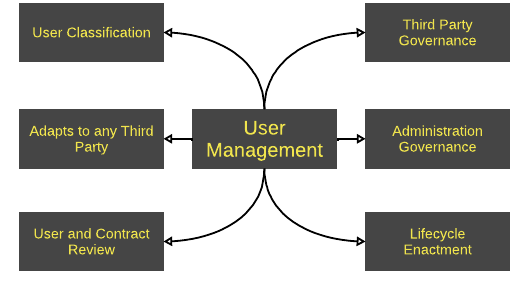
User management
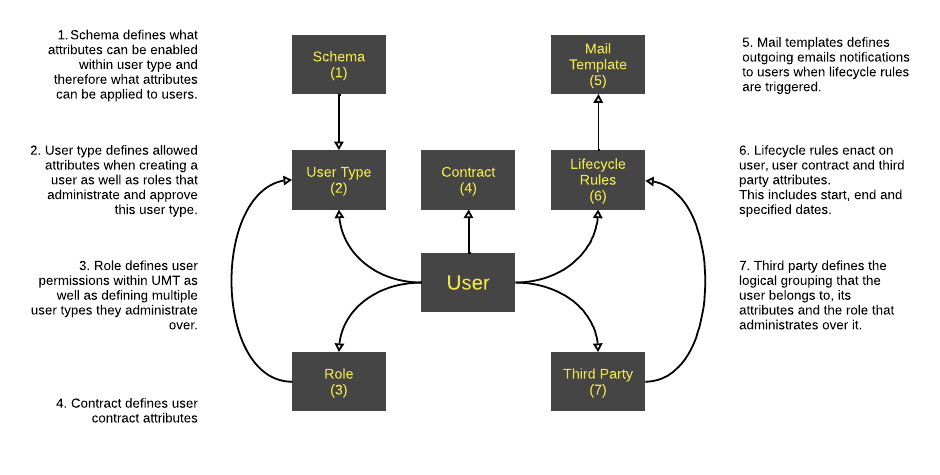
New users can be generated quickly with the correct account type and the required level of access to perform their role as defined. Attributes associated with the user can be configured to only collect the minimal information required, simplifying user creation.
Third parties are managed within a simple structure, with no orphan accounts unconnected to any administrator. Users are assigned to administrators based upon their user type creating a chain of responsibility.
When an administrator creates a new user, the request is sent to an appropriate user who can approve or deny the request. This removes the need to complete various time consuming forms, ensuring effective governance of administrators.
Lifecycle rules ensure that the correct level of access is provided by updating the UMT database. Access is granted upon the user's or third party's start date and revoked upon the user's or third party's end date. This information is provided to the IT department along with a notification to approve or remove access to the users listed. This ensures that users can access systems immediately along with revoking access when it is no longer required.
Lifecycle rules help enact reviews of third parties, their users and contracts. This ensures that third parties and their users are assessed periodically to see if it is still appropriate for them to have certain levels of access.
UMT is a highly adaptable tool, that is configurable to any type of third party and their users, allowing for effective governance.
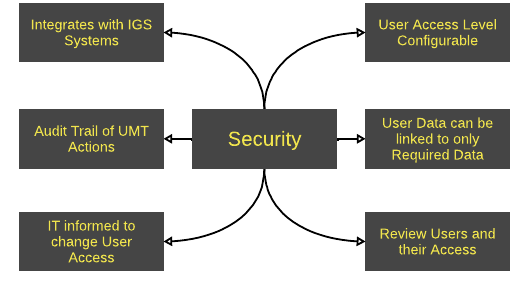
Security
UMT supports OIDC Identity Providers such as IBM Verify, Okta, and Entra ID. All data is encrypted at rest and in transit.
The level of access within UMT granted to users is customised to their requirements. Meaning actions and data available to them is restricted to only what they require to perform their role.
The attributes associated with the user can be configured to only collect the minimal required, reducing the severity of any potential data breaches as no surplus data is stored.
Lifecycle rules prompt management to review user access and rectify it if necessary, helping to ensure compliance with company security policies. In doing so, we reduce the risk of data being exposed to user who are no longer associated with the business through lingering access rights.
Changes within UMT are recorded and can be presented in a report which can then be exported to a Security Information and Event Management (SIEM) tool to monitor for suspicious activity so that actions can be taken to prevent data breaches or security breaches.
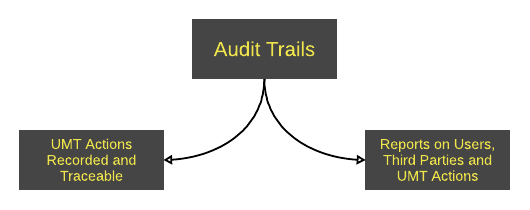
Audit trails
Actions and changes within UMT are recorded and can be traced. This includes requests such as adding or modifying users and request approvals or denials. Along with who was the requestor, approver, beneficiary and the date of the actions. This ensures that processes within the organisation can be tracked and traced back to their origin so to assess that actions taken are correct.
Reports can be generated to provide a detailed overview for all users, specific users, third parties and the actions taken within UMT.