Use cases
Madigan's user management tool (UMT) can be broadly applicable to several different types of organisations.
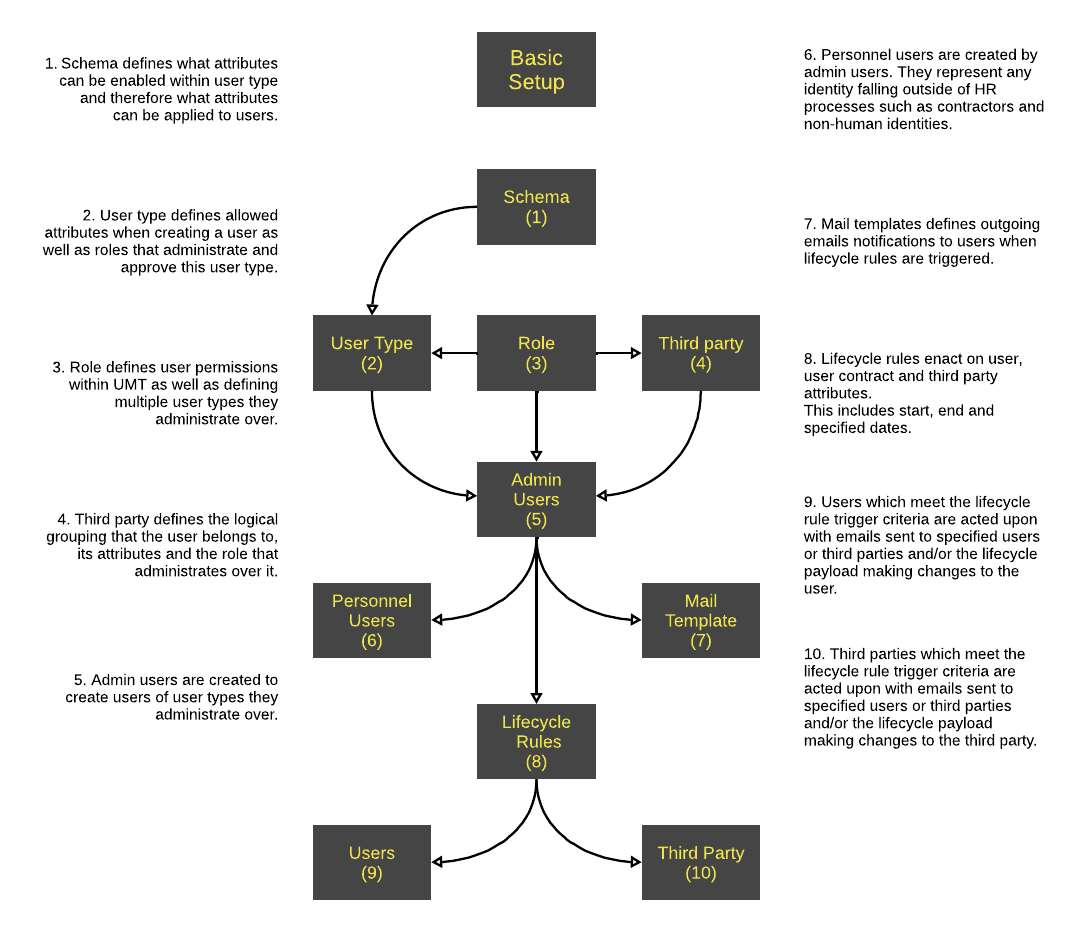
Below is the structure of a basic setup of UMT.
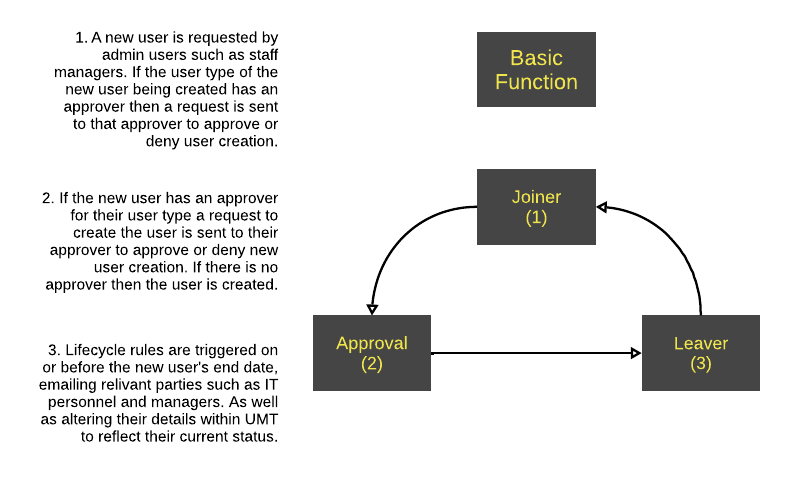
Below is the basic function of UMT.
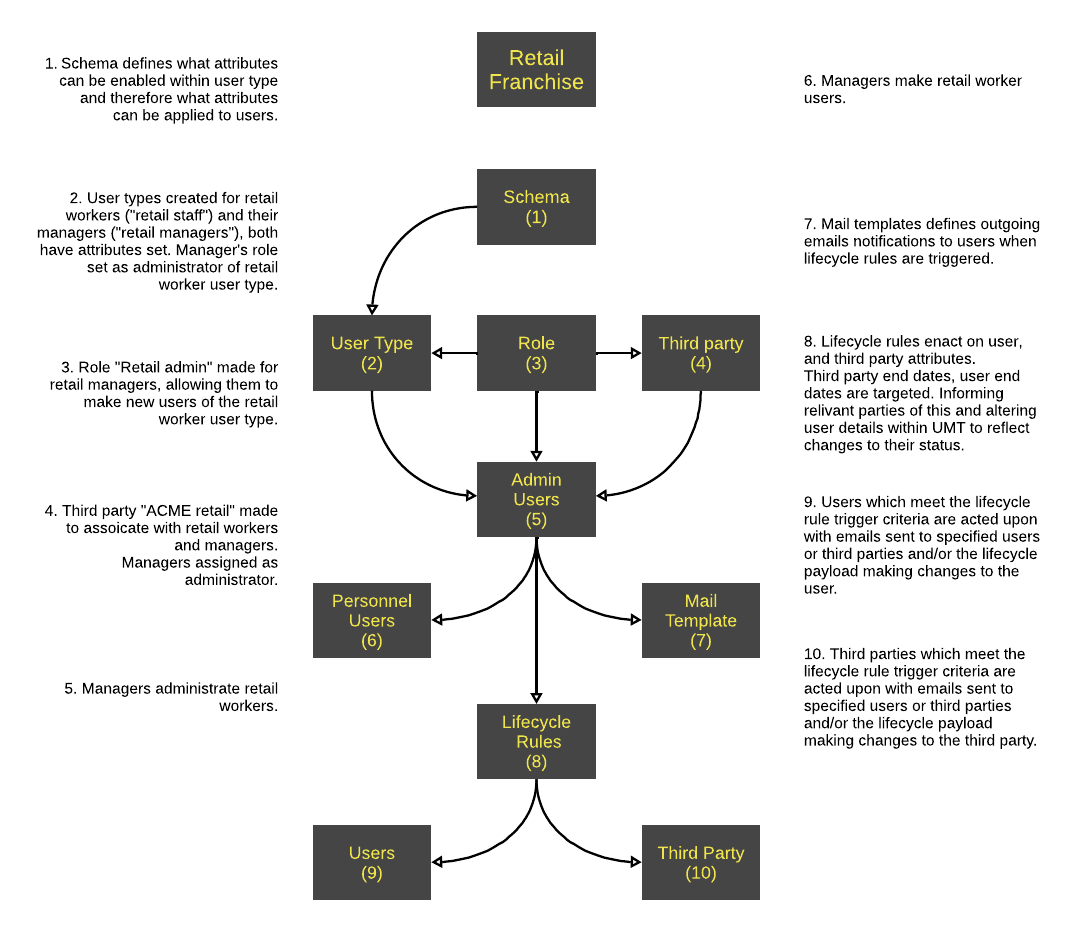
Retail franchises
Due to seasonal demands, retail franchises experience high intakes of workers and their employee churn rate is high - 20% of employees leave within six weeks of being hired.
UMT Lifecycle Rules can simplify managing a constant stream of workers joining and leaving.
Lifecycle rules can be written to trigger before, on and after a worker's start and end dates. This means that managers can be notified on workers are going to be leaving or joining.
The IT department can be notified to grant or revoke access to workers and lifecycle rules update the user's details within the UMT database so that the IT department has enough information to make necessary actions.
High numbers of workers can be produced quickly by bulk adding them which eases the pressure during high seasonal worker intake periods.
When administrators create new staff, a request to create them can be sent to the franchise manager to for their approval.
All actions with UMT are all recorded and ready to be presented in a report which can be scheduled to generate periodically, allowing for retail franchises to monitor their staffing and trends within.
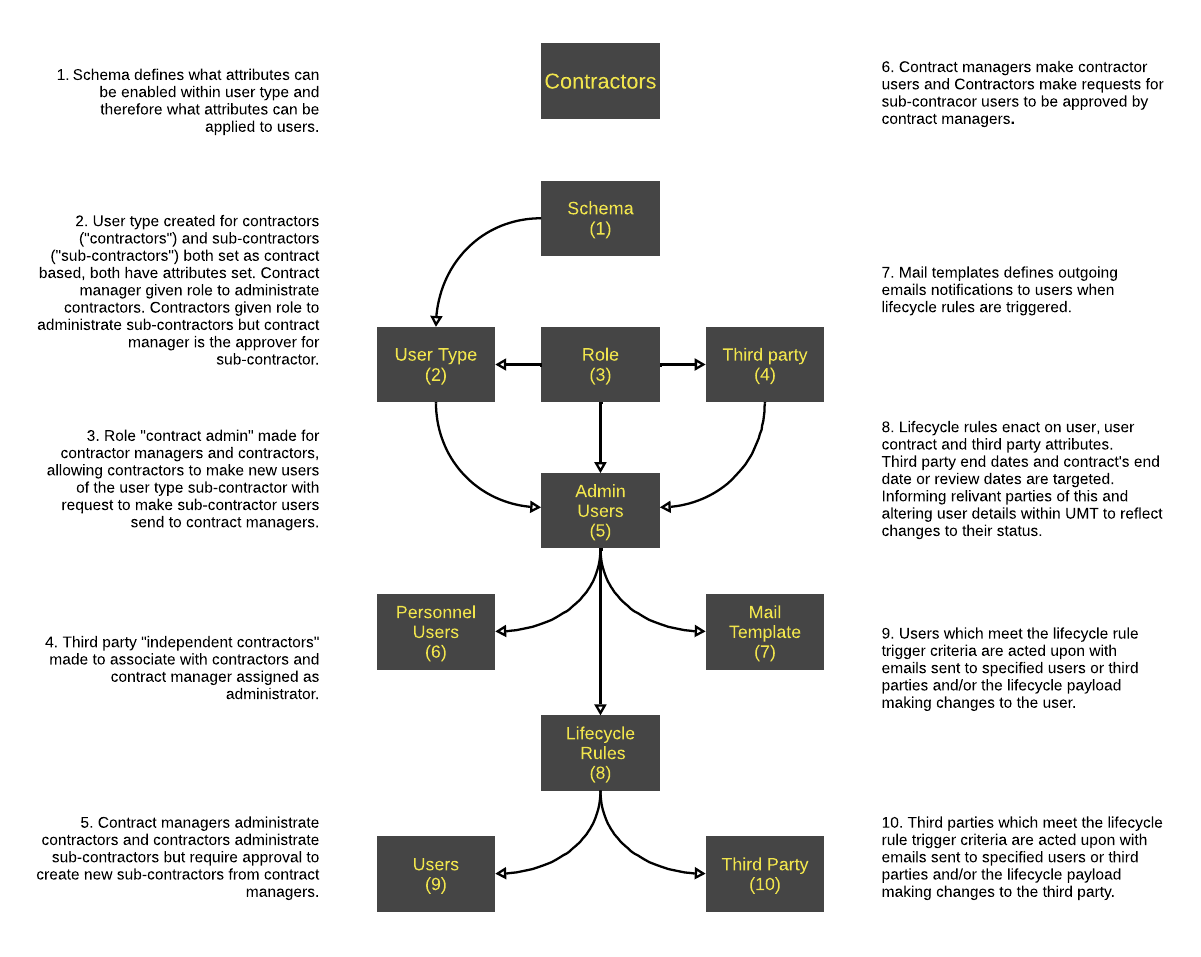
Contractors
Contractors are highly skilled specialist workers that are typically employed for short periods or until project completion.
Contractors themselves can hire sub-contractors which have different expertise to them. This can lead to several layers of contracts each requiring approval and periodic review.
UMT Lifecycle rules can simplify contract and sub-contract management.
Lifecycle rules can be written to trigger before, on and after a contractor's contract's start and end dates as well as trigger on a review date. This means contract managers can be notified when a contractor or sub-contractor is joining or leaving as well as if the contract needs to be reviewed for renewal, termination or re-negotiation and to assess performance levels.
The IT department can be notified to grant or revoke access to contractors or sub-contractors and lifecycle rules update the contractor's and sub-contractor's details within the UMT database so that the IT department has enough information to make necessary actions.
Furthermore, when contractors create sub-contractors, a request to create them can be sent to the appropriate approver.
Contracts store who requested and approved the contract showing the responsible parties as well as notes on the contract for further context such as existing or developing risks, issues and possible delays.
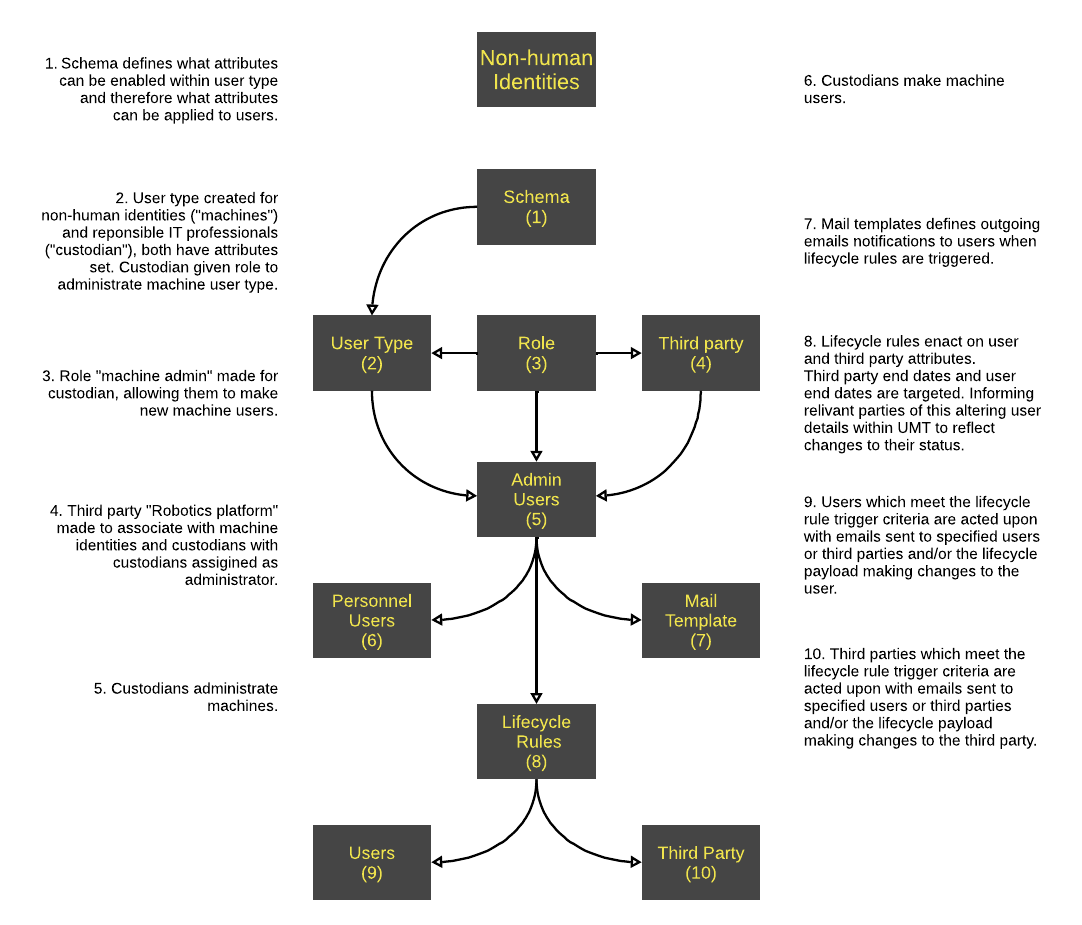
Non-Humans
By 2025 it is estimated that there will be 75 billion machine identities and within organisations they can outnumber human identities fifty to one.
Managing them can prove difficult with their sheer volume which solutions would have to scale to and the high risk of oversight due to low visibility of machines that exist within an organisation.
Oversights such as excessive access than needed and redundant machines in use.
UMT Lifecycle Rules can simplify Non-Human Identity Management.
Lifecycle rules can be written to trigger before, on and after a machine's start and end dates as well as trigger on a review date. This means that the IT department or machine custodian can be notified when a machine is being activated or deactivated and which machines to grant or revoke access to or need to be reviewed to assess that level of access is appropriate and that they are still required.
Lifecycle rules update the machine's details within the UMT database so that the IT department or machine custodian has enough information to make necessary actions.
The high volumes of machine identities can be scaled with by bulk adding them and the Lifecycle Rules can target any number of machine identities.
UMT increases the visibility and identification of non-human identities within organisations displaying their functions, level of access, who is responsible for them and their attributes.
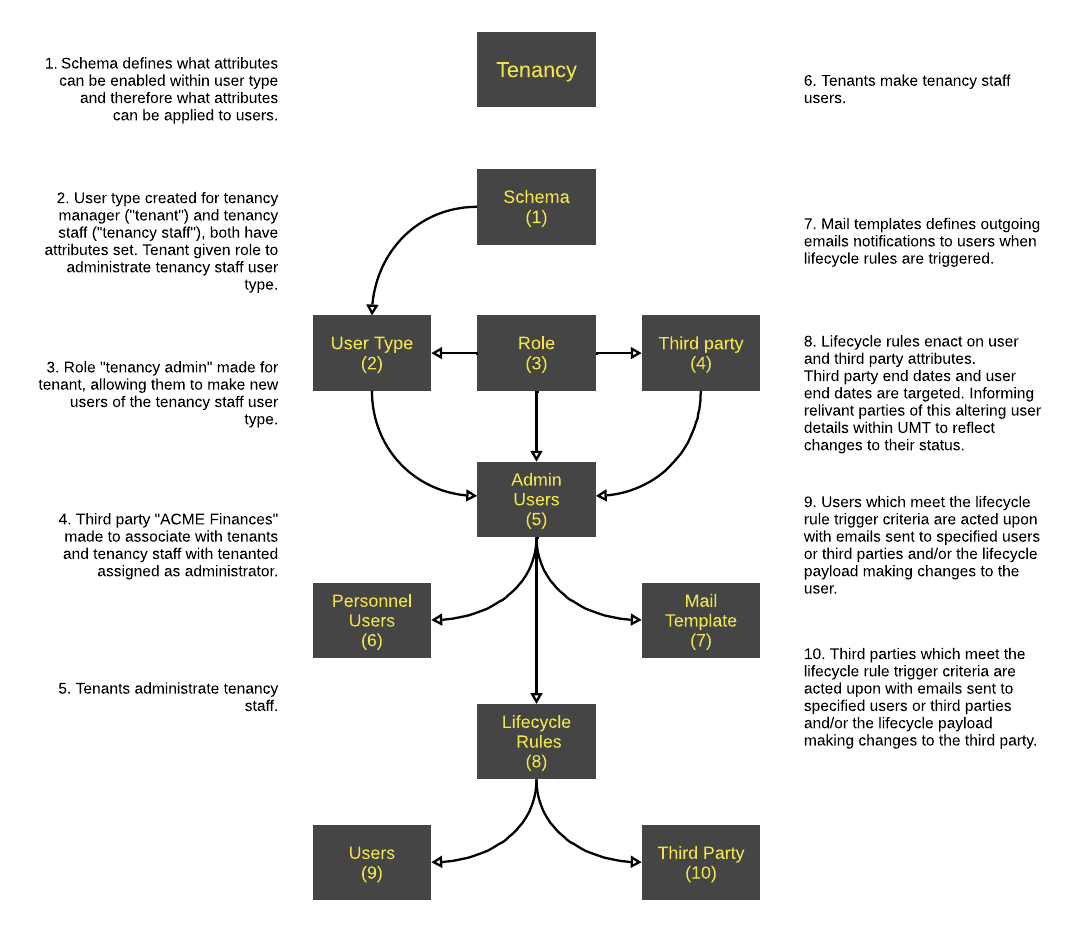
Tenants
Tenants are office tenants, students and any other groups that require access to an organisation and its facilities but are not direct members of it. They can require physical access to sites therefore needing to be issued key cards or Fob keys (Frequency Operated Button) to be granted access by the premises keyless entry system. These electronic keys are configured to only give access to certain areas and rooms depending on the access requirement of the tenant.
They can require virtual access to on-site facilities such as an account made for them to access local wi-fi and integrate with local systems such as printers and computers.
Also the tenancy can require periodic renewal especially if the tenants are paying for access to an organisation.
UMT Lifecycle Rules can simplify Tenant Management.
Lifecycle rules can be written to trigger before, on and after a tenant's start and end dates as well as trigger on a renewal date. This means tenant managers can be notified when a tenancy is starting or when their members are joining or leaving the tenancy as well as if the tenancy needs to be renewed.
IT department can be notified to grant access or revoke access to tenants and their members and lifecycle rules update the tenancy's and their members' details within the UMT database so that the IT department has enough information to make necessary actions.
UMT increases the visibility of third parties and their members and aids in granting access or removing their access and permissions as soon as it is required.